

Check out our quick guide to understand what Salesforce Transactions Security Policies are and how can we create one.
Transaction Security on salesforce is a framework that allows you to monitor and subscribe to user activity, intercept in real-time and take an action based on certain events.
It’s easy to set up with a few clicks via condition builder, or with custom apex code for more complex scenarios.
When creating a transaction security policy, you first pick a transaction or event to watch for and then you choose actions that are triggered when the event occurs.
For example, a common security risk case happens when users are allowed to export large volumes of data via reports (exporting a report as in excel sheet to their desktop for example), and this data can no longer be protected by salesforce.
To prevent that from happening, a transaction security policy can be easily set up on the report event to prevent users from exporting reports that has x or more rows, or simply set it up so that you are notified when such event occurs.
API events monitor API transactions, such as SOQL queries and data exports. More info.
API anomaly event policies monitor anomalies in how users make API calls. More info.
Bulk API Result Event policies detect when a user downloads the results of a Bulk API request. More info.
Credential stuffing event policies monitor when a user successfully logs into Salesforce during an identified credential stuffing attack. Credential stuffing refers to large-scale automated login requests using stolen user credentials. More info.
List View event policies monitor when data is viewed or downloaded from your list views using Salesforce Classic, Lightning Experience, or the API. More info.
Login event policies track login activity and enforce your org’s login requirements. More info.
Permission set event policies monitor when users are assigned critical permissions in a permission set. More info.
Report event policies monitor when data is viewed or downloaded from your reports. More info.
Report anomaly event policies monitor anomalies in how users run or export reports. More info.
Session hijacking event policies monitor when unauthorized users gain ownership of a Salesforce user’s session with a stolen session identifier. More info.
Condition Builder is a Setup feature that allows you to build policies with clicks, not code.
When you build your policy using Condition Builder, you choose which fields on these objects you want to monitor for customer activity. Because your policy’s actions are conditional to the fields that users interact with, these fields are called conditions.
However, the conditions available in Condition Builder are a subset of all the event objects fields and vary based on the objects, while if you create a policy based on apex code, you can use any of the event object’s fields.
For example:
Records isn’t available as a Condition Builder condition for the ReportEvent event object however, you can use the ReportEvent.Records field in an Apex class that implements the TxnSecurity.EventCondition interface.
The CEO of a company asked the administrator of their salesforce org to implement a security measure that would prevent large data exports, and he would also like to be notified whenever such action takes place.
The salesforce administrator decides to setup a Transaction security policy of type “Report Event” that would block any users from exporting reports that has 100 or more rows and would notify the relative salesforce user about this breach.
We set the following parameters:
-Event : Report Event
-Condition Logic : All Conditions are Met (And)
-Condition 1: Operation Equals “ReportExported”
-Condition 2 : Rows Processed Greater than or equal “100”
Then press Next
We choose the “Block” Action
for block message, we can either keep the default block message, or choose a custom block message that appears to the user whenever the action takes place and is blocked.
Next, we specify the way we want the user to be notified
in our case, we’ll be both sending an Email and notifying the user in Salesforce and choose the user we want to be notified under “Recipient”.
Then, we choose the type of email we want the user to receive
We can either keep the default email content, or specify our custom Email message content
Finally, we specify a name and Description for our Transaction security policy, set Status to “Enabled” and press Finish.
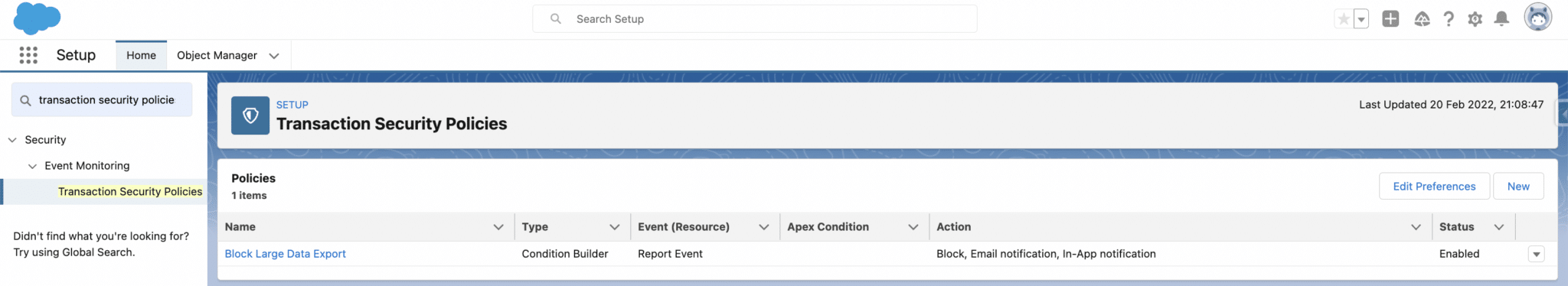
Now, whenever a user tries to export a report that meets the conditions, three things will happen:
1- The action will be blocked, and the user will be redirected to a page with the custom message we set:
2- the user we set as recipient will receive an in-app notification in salesforce:
3- they will also receive an email notifying them about the breach:
That is all for now, thank you for your time and we hope you learned some new cool tricks on Salesforce platform. Stay tune! we will expand our Salesforce Transactions Policy guide with different scenarios in future articles.
In Nubessom we have more than 10 years helping companies around the world achieve their Salesforce, CRM and business automation needs.
We are your trusted Salesforce consulting partner, please reach us by clicking here or in our contact form below.

Alex is one of the key members at Nubessom, he has passion to learn new features and mentoring his peer colleagues, and enjoys helping clients to automate everything CRM related!




© 2025 Nubessom All Rights Reserved